Artner Co., Ltd. (hereinafter referred to as “the Company”) has a management philosophy of contributing to society through its engineers. To do so, it is essential that we handle information assets properly and maintain the trust of our customers. As a means to this end, we have established the policy on information security, which will be promoted through company-wide efforts.
The Company’s specific policy on information security
|
1.
|
1.
|
Scope
The “information assets” covered by this policy refers to all information held by the Company and customer information obtained in the course of the Company’s business. All employees of the Company (including executives, contractors, and part-time employees) must comply with this policy.
|
|
2.
|
Management system
The Company establishes an information security management system as a system to execute this policy.
The information system is implemented and managed under the information system department under the guidance of the information system administrator.
(Organizations managing the information system)
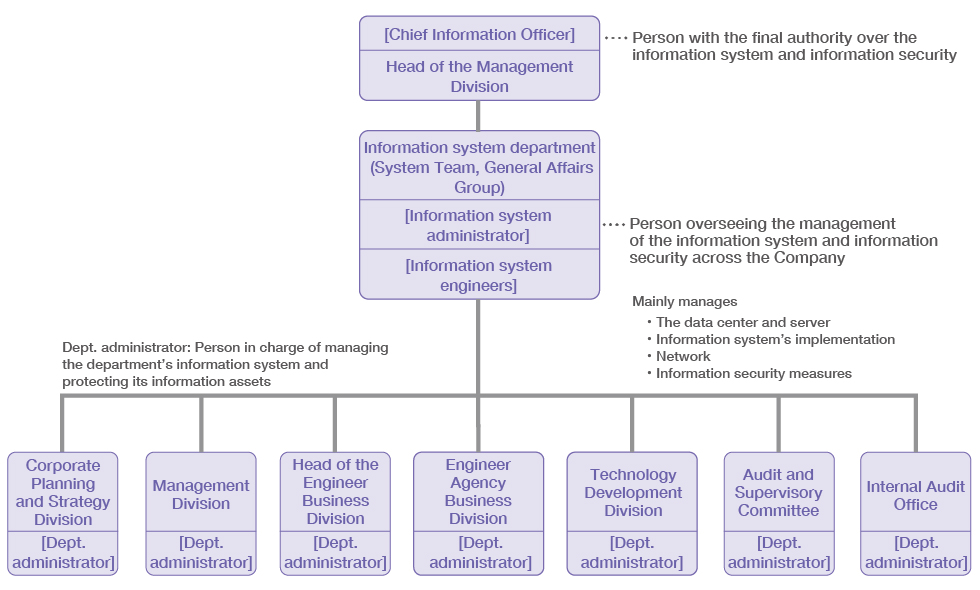
|
|
3.
|
Compliance with laws and regulations
The Company will comply with laws, regulations, and codes related to the protection of information assets, establish specific internal rules, and take a strict stance against any violations.
|
|
4.
|
Education and raising awareness
The Company will provide thorough and ongoing security education to all employees to raise their level of awareness.
The information system administrator and members of the information system department will continuously receive education and attend outside seminars to learn about the methods and techniques of system management. A summary of the education provided by the Company and received by employees will be prepared and reported to the Chief Information Officer.
(Security education for all employees)
・All employees will take the e-learning “Information Security Course” every year
・The information security policy and privacy policy will be informed to employees during their training upon entering the Company
・Employees with submit monthly checklists to increase their awareness of information security
(Security education for the managing department)
・Periodic education and training on cyberattacks (e.g., training to counter targeted attack e-mails)
|
|
5.
|
Audit and improvement
The Company will set access rights to information assets for each employee and carry out audits through access logs and alerts. In addition, the Company will periodically audit its information security management system to ensure its proper operation and improvement, and maintain its effectiveness.
|
|
6.
|
Incident response
The Company will strive to prevent information security incidents. In the event of an incident, we will do our best to minimize the scope of the impact, recover promptly, and take preventive measures.
|
|
7.
|
Backup system
The Company will make distributed backups of information assets and the information system and strive to achieve a quick recovery in the event of an information security incident or natural disaster.
|
Cybersecurity readiness
Based on the above policy, the Company will take the following measures for cybersecurity readiness.
|
|
1.
|
|
1.
|
Monitoring
The information system administrator will detect accidents and failures through daily monitoring at fixed times, including monitoring the status of the server, network, and other information system components and the backup status.
Furthermore, the Company will carry out behavior monitoring at endpoints, which become the starting point of security incidents. In the event of an abnormality, we will take emergency measures, such as immediate network shutdowns, to minimize any damages.
|
|
2.
|
Response to incidents
In the event of an incident related to information security, the information system administrator will immediately report it to the Chief Information Officer and take the following actions:
(1) If there is a risk that unauthorized access and viruses, etc., may spread through the network and cause damage to information assets, immediately disconnect the network for protection.
(2) If information assets or the information system cannot be accessed due to a natural disaster or other incidents, immediately create a detour route or alternative means and strive to make a recovery.
(3) If information assets are lost, immediately attempt to recover them from the backup.
(4) Following the incident, summarize the status, response measures, and recurrence prevention measures for the occurred incident, report them to the Board of Directors, and promptly implement the measures.
|
|
3.
|
Use and management of equipment
The Company will take the following actions to prevent information security incidents from occurring:
(1) Network isolation and communication control by equipment
(2) Antivirus measures and behavior monitoring
(3) Equipment software updates
(4) Prohibit connecting equipment to unauthorized networks
(5) Restrict equipment connected by authentication for remote access
(6) Prohibit bringing your own device (BYOD)
|


